Credit Card Heist: Analysis of an IIS Backdoor Incident

In recent years, data breaches have become increasingly common, from hacked databases and large-scale data dumps to consumer personal information leakage on the dark web, leaving businesses and users alike in a state of unease. Traditionally, financial institutions have focused on securing databases to prevent massive data leaks. However, a recent incident we handled has challenged this. Instead of targeting the database, hackers used a backdoor module lurking in an IIS server to intercept credit card information directly during transactions. This "on-the-fly" theft technique is stealthier, more precise, posing a significant challenge to existing defense systems.
This article dives into a recent credit card data breach targeting a hybrid cloud-on-premises infrastructure, reconstructing the attack path and analyzing the malicious programs and techniques employed by the attackers.
Incident Background
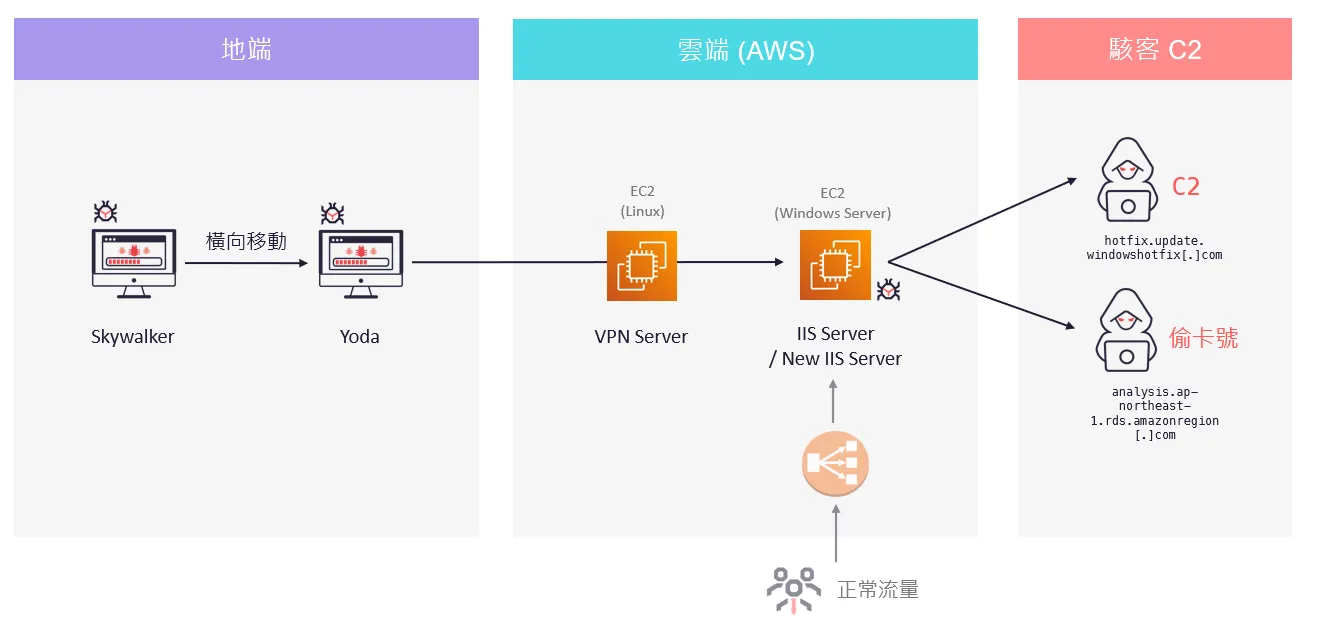
It was a hybrid cloud environment where on-premises ran a traditional Windows Active Directory (AD) domain and cloud infrastructure was built on AWS. The cloud-based IIS server handled credit card transactions, with normal traffic routing through an AWS Load Balancer. The on-premises environment connected to the cloud IIS server via a VPN server for application deployment and management. Notably, despite the integration of AWS cloud services, core businesses still ran on Windows Server IIS servers hosted on EC2 instances. As a result, the investigation of this incident closely resembled traditional Windows environment analysis.
During the investigation, we identified two types of malicious programs on this IIS server:
- IIS Backdoor Module: A malicious IIS module designed to steal credit card numbers.
- Backdoor Program: A backdoor with command-and-control (C2) connectivity, used to maintain persistent access and receive remote instructions.
Our findings revealed that the attackers did not directly breach the cloud environment from the outside. Instead, they first infiltrated the on-premises environment, then moved laterally to eventually reach the cloud-based IIS server handling sensitive data.
Lateral Movement

While the initial entry point was difficult to pinpoint, evidence suggests that attackers used Remote Desktop Protocol (RDP) as their primary method for lateral movement. We observed successful RDP logins across multiple systems in the environment, through which the attackers deployed the backdoor program. It’s speculated that the attackers may have exploited weak passwords, credential theft, or other methods for initial access, though the exact method still needs further analysis.
The attackers ultimately used the cloud VPN server as a jump point to connect to the cloud IIS server, again leveraging RDP to deploy the backdoor program in the cloud environment. This indicates a high level of familiarity with the infrastructure.
IIS Backdoor Module

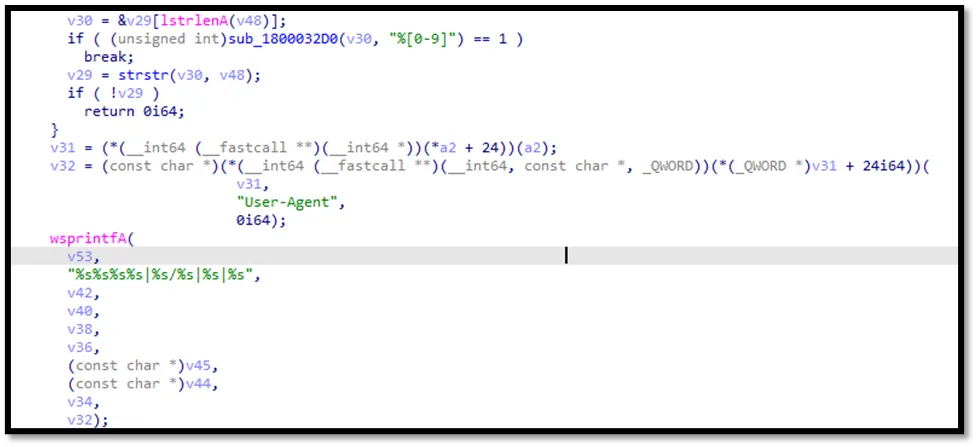
The attackers delicately installed a malicious IIS module in the IIS server. This module hooked into the OnPostBeginRequest function of the IIS process, enabling it to intercept and inspect the content of every incoming HTTP request in real time. The module’s core function was to log requests containing credit card information. Specifically, it recorded the request content, including credit card numbers, along with the User-Agent string and timestamp, into a file saved at C:\Users\Public\Libraries\crash.dmp.

To avoid pattern-based detections, the attackers applied a simple XOR 0xa1 operation to obfuscate the file’s contents. Naming the file crash.dmp was a deliberate strategy to disguise it as a system crash memory dump, reducing suspicion from security analysts.
Additionally, the malicious module transmitted stolen data to analysis.ap-northeast-1.rds.amazonregion[.]com. Notably, this domain used the same AWS region (ap-northeast-1) as the environment, indicating thorough investigation and customization by the attackers.

In the IIS configuration of file web.config, we found that the attackers appended a line to the <globalModules> section to load a module named warmup.dll. This ensured the malicious module was automatically loaded when IIS started, achieving persistent.
Backdoor Program

In addition to the IIS backdoor module, the attackers deployed a backdoor program named VsGraphicsProxyStub.dll, which was loaded via DLL with a signed executable, MpDefenderPushService.exe.

Both VsGraphicsProxyStub.dll and MpDefenderPushService.exe were placed in the directory of C:\Program Files\Windows Defender Advanced Threat Protection\Classification. Despite its name, MpDefenderPushService.exe was actually a renamed version of Visual Studio’s VsGraphicsDesktopEngine.exe, repurposed by the attackers to avoid detection. The chosen directory was writable by members of the Administrators group, unlike the Defender-protected C:\Program Files\Windows Defender directory, making it an ideal access for the attackers.
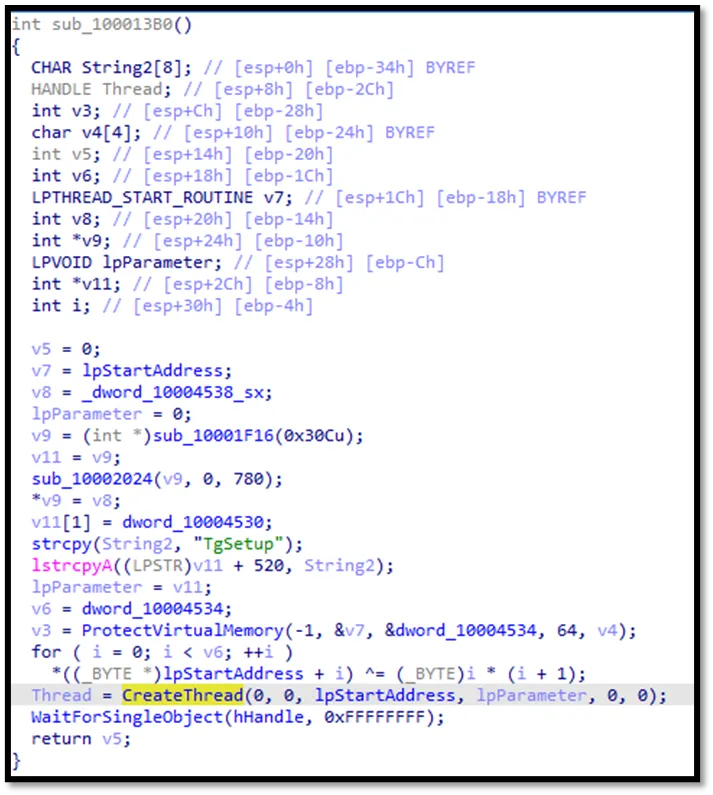

Upon execution, VsGraphicsProxyStub.dll loaded a file named Pbsyfffinltsufq, which is composed of encoded shellcode. This shellcode used the RtlDecompressBuffer function to decompress and execute a file named sxqwgmyu, a second-stage PE executable (the actual backdoor).


The backdoor could communicate with a C2 server at hotfix.update.windowshotfix[.]com via SSL-encrypted connections, having the ability to download and execute additional shellcode modules, demonstrating extensibility and the ability to execute remote control.

For the persistent, the backdoor registered itself as a Windows service named "Microsoft Defender Push Service."
Conclusion
With the rise in personal data breaches, financial institutions, due to their economic value, remain prime targets for hackers. This article uses the IIS backdoor case to illustrate how attackers target financial entities to steal credit card information and outlines their tactics, techniques, and procedures (TTPs). We emphasize three key takeaways:
- Hybrid Infrastructure Risks: As financial institutions increasingly adopt cloud services, the security of hybrid cloud infrastructures has become a critical concern. This incident highlights how attackers exploit such configuration.
- On-the-Fly Theft: The use of a backdoor module in an IIS server to intercept credit card data during transactions, bypassing the need to access databases, represents a stealthy and efficient attack method.
- Emerging Trends: Recent monitoring has identified similar IIS server backdoor attacks in other incidents, underscoring the growing prevalence of this technique.
For more information, you can visit CyCraft’s blog: https://www.cycraft.com/en/blog.
IOC
- hotfix.update.windowshotfix[.]com
- analysis.ap-northeast-1.rds.amazonregion[.]com
- ee0a7b69a82bf84abb7d77dc907b6e69 (MpDefenderPushService.exe)
- 6a9881877e6bed705a42f3293263acc8 (VsGraphicsProxyStub.dll)
- 81b13fee07bd38dee08d615e54978be3 (warmup.dll)
Writer: Alien Chao
CyCraftについて
CyCraft(サイクラフト)は、AIによる自動化技術を専門とするサイバーセキュリティ企業。2017年に設立され、台湾に本社、日本とシンガポールに海外拠点を持つ。アジア太平洋地域の政府機関、警察・防衛機関、銀行、ハイテク製造業にサービスを提供している。CyCraft の AI技術 と機械学習技術によるソリューションが評価され、CID グループ とテマセク・ホールディングス旗下のパビリオンキャピタルから強力なサポートを獲得し、また、国際的トップ研究機構である Gartner、 IDC、Frost & Sullivan などから複数の項目において評価を受けている他、国内外の著名な賞をいくつも受賞している。また、国内外を含む複数のセキュリティコミュニティ、カンファレンスに参画し、長年にわたりセキュリティ業界の発展に尽力している。

