【CyCraft Monthly Intelligence】Attacking Asia with AI: Analysis of Emerging UTA0388 Threat

Threat and Impact
Since June 2025, UTA0388 has launched a series of spear-phishing campaigns. While their targets span across North America and Europe, they primarily focus on Asia. This Chinese-linked adversarial group utilizes advanced social engineering techniques, including the fabrication of personas and institutions to deceive targets into executing malicious programs.
Once a target system is successfully compromised, UTA0388 gains remote access to the victim's internal network to conduct espionage, steal sensitive data, or cause operational disruptions. Their focus on Asian geopolitics, particularly Taiwan, underscores a strategic intent aligned with national interests. These attacks span multiple countries and languages, posing a significant impact on global governments, research institutions, and private corporations.
Analyst Perspective
UTA0388 is a continuously evolving threat group that combines sophisticated rapport-building phishing, LLM-driven automated attacks, and advanced malware deployment. Although this attacker currently targets Asia, organizations worldwide must remain vigilant against related social engineering. A successful breach can lead to unauthorized network control, data exfiltration, and potential geopolitical conflicts.
Incident Description
The techniques of UTA0388 have evolved over time, shifting from traditional spear-phishing (sending emails with malicious links) to rapport-building phishing. This method involves establishing trust through harmless initial correspondence before sending actual malicious code or malware. This strategy allows the attackers to delay the exposure of their infrastructure and increase the probability of a successful breach.
A defining characteristic of UTA0388’s operations is the use of LLM to automate the generation of phishing emails and malware components. The phishing messages often exhibit linguistic inconsistencies, nonsensical content, and fabricated details, indicating AI-generated text produced without human oversight. The massive volume and rapid path of these attacks further highlight their automated operations.
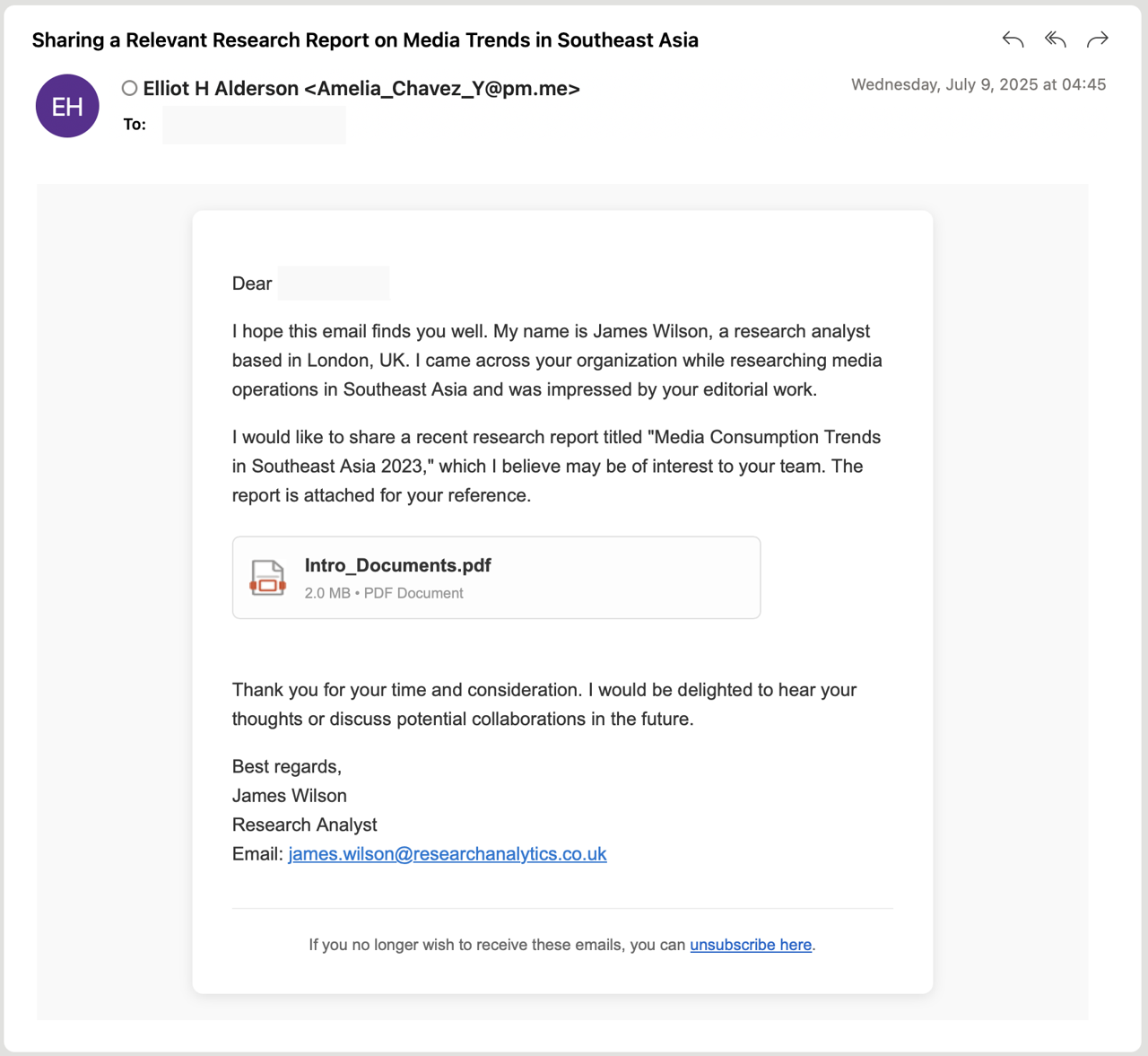
UTA0388 sends highly customized, multilingual emails (including English, Chinese, Japanese, French, and German) based on the victim's habits, often impersonating senior researchers or analysts from non-existent institutions (Figure 1). These emails contain links to cloud storage that, once opened, deploys the backdoor GOVERSHELL.
GOVERSHELL is the primary malware family used in these attacks and is evolving rapidly. At least five distinct variants have been observed, each featuring different C2 communication methods, with enhanced persistence and improved remote command execution capabilities.

Technical Details
To provide a systematic and thorough understanding of the entire process, from initial targeting and malware deployment to the communication establishment, this section follows the tactical categories of the MITRE ATT&CK. Technical details include the root cause, UTA0388’s attack techniques, characteristics of the GOVERSHELL malware family, and how UTA0388 leverages LLMs to assist their operations.
Reconnaissance
UTA0388 begins by gathering large-scale intelligence to identify potential targets in North America, Asia, and Europe, followed by in-depth analysis and strategy formulation. The attackers collect public email addresses from various sources, including organizational websites, group contacts, outdated employee accounts, and even templates or non-functional email formats. This indiscriminate, large-scale collection suggests the use of partially automated tools with limited context awareness, consistent with the characteristics of LLMs or automated scraping tools. These reconnaissance efforts not only gather data but also facilitate the design of rapport-building phishing contents.
Resource Development
While details on resource development are limited, the campaign shows that UTA0388 has established multiple resources to support its operations. Many domains registered and controlled by UTA0388 exhibit the following traits:
- Taiwan-related names: moctw[.]info and twmoc[.]info.
- Impersonation of major organizations or legitimate services: cdn-apple[.]info, azure-app[.]store, doccloude[.]info, sliddeshare[.]online, and windows-app[.]store.
The attackers also host phishing content and malware on various cloud platforms (Netlify, OneDrive, and Sync) and utilize trusted webmail providers like ProtonMail, Outlook, and Gmail to send spear-phishing emails. They meticulously manage this infrastructure, consistently registering domains through Cloudflare to evade tracking and takedown.
Initial Access
The primary inital entry of UTA0388 is spear-phishing. Targets receive highly customized emails impersonating senior researchers or analysts from fictitious institutions. These emails contain links directing recipients to cloud-hosted archives (ZIP or RAR files) containing a seemingly legitimate executable and a hidden DLL that utilizes Search Order Hijacking to execute malicious code.
The delivery is quite simple: social engineering lures users into clicking links, downloading archives, and running the seemingly-harmless executable, which triggers the malicious DLL. In rapport-building variants, attackers engage in multiple email exchanges to build trust before sending the malicious link, significantly increasing the infection success rate.
Execution
The key to execution is “Search Order Hijacking.” The delivered package includes a legitimate executable named to mimic important organizational documents or topics relevant to the target (e.g., Asian geopolitical issues). When the user runs the file, the Windows DLL search order prioritizes loading the malicious DLL located in a hidden lib directory instead of the intended legitimate DLL. This hijack executes the GOVERSHELL backdoor, allowing attackers to run remote commands. To improve stealth, variants often use legitimate open-source executables (such as Tablacus Explorer) during the execution.
Persistence
The GOVERSHELL backdoor establishes scheduled tasks during the system startup or on a periodic basis, allowing the attacker to maintain a long-term persistence on the victim's device. These tasks include specific parameters to ensure that C2 logic only activates after the initial setup. This design also evades sandbox dynamic detection, as the malware exits immediately during its first execution without initiating C2 communication, thereby hiding its malicious behavior.
Defense Evasion
UTA0388 employs multiple evasion techniques:
- Search Order Hijacking: Blending malicious execution into legitimate processes to bypass process monitoring tools.
- Use of Legitimate Cloud Services: Hosting malware on reputable platforms like Netlify, OneDrive and Sync helps blend malicious traffic with trusted network activity.
- Scheduled Tasks with Delayed C2: Using internal parameters to delay C2 communication reduces the likelihood of early discovery by sandboxes or EDR systems.
- Leveraging Multiple Email Providers: Distributing phishing emails across various major services reduces the risk of detection and makes email filtering more challenging.
Command and Control (C2)
The GOVERSHELL C2 infrastructure has undergone several iterations, with each variant introducing different communication methods to evade detection and stabilize control:
- Variant 1 (Early/HealthKick): Use pseudo-TLS with dual headers and XOR encoding via port 465.
- Variant 2 (TE32): Employ pseudo-TLS encrypted with AES via port 443.
- Variant 3 (TE64): Utilize HTTPS POST requests with periodic JSON reporting.
- Variant 4 (WebSocket): Use AES-encrypted WebSocket connections and introduce a command task queue model.
- Variant 5 (Beacon): Send data via Base64-encrypted HTTPS GET requests with randomized connection intervals.
Initially, C2 communication used direct IP connections, but since mid 2025, the group has shifted to domain names hidden behind Cloudflare. Additionally, the WebSocket variant's C2 server responds with messages like "Secure C2 Server is running," indicating active monitoring.
Impact
The main impact is the establishment of persistent remote access via the GOVERSHELL backdoor. UTA0388 can execute arbitrary commands to conduct espionage, data theft, or network intrusion in line with its geopolitical objectives. Their continuous development of multiple malware variants demonstrates a clear intent to maintain a long-term presence and expand their footprint within target environments.
Other Technical Observations
- AI-assisted Attacks: Evidence confirms UTA0388 uses LLMs (specifically OpenAI’s ChatGPT) to generate phishing content and assist in malware development.
- Inconsistencies in multilingual content, fabricated personas, and nonsensical attachments (such as pornographic images with text overlays, Buddhist chants, or meaningless text files) are likely remnants of automated generation processes.
- The rapid development and variability of the GOVERSHELL network stack and codebase suggest AI assistance.
- The transition from C++ to Golang and the tendency to rewrite rather than iterate on code aligns with the characteristics of AI-generated output.
- Geopolitical Targeting and Attribution: The presence of Simplified Chinese in developer logs, the focus on Taiwan and Asian geopolitics, and links between UTA0388 infrastructure and known pro-China threat groups provide high confidence regarding the origin of these attacks.
Conclusion
UTA0388 represents an evolving threat that leverages LLM-generated content for spear-phishing and deploys sophisticated GOVERSHELL backdoors using advanced persistence and C2 techniques. The root cause remains social engineering: deceiving users into executing files that use Search Order Hijacking. The technical complexity of this malware family, combined with AI-driven phishing, signals a new era of "Human-AI Collaboration" in cyber warfare.
Mitigation
Given the complexity of UTA0388 operations, organizations must implement a multi-layered defense to mitigate risks associated with such targeted attacks. Protecting sensitive information and maintaining the integrity of critical systems requires a proactive and vigilant security posture.
- Enhance Email Security
Deploy advanced email security solutions capable of detecting and intercepting suspicious links and attachments:- Obfuscated URL Detection: Implement systems that can identify and block obfuscated or dynamically generated URLs.
- Attachment Scanning: Automatically scan attachments to check for known malware and suspicious file.
- Network Monitoring and Detection
Deploy robust network monitoring tools to detect and respond to anomalous activities:- Endpoint Detection and Response (EDR): Deploy EDR tools to monitor and respond to suspicious activities on host machines.
- Behavioral Analytics: Employ techniques that detect deviations from normal user behavior, which may indicate that a system has been compromised.
- User Awareness and Training
Educate employees on the latest phishing tactics and emphasize the importance of maintaining high vigilance:- Regular Training: Conduct periodic training on how to identify phishing attempts and report suspicious activity.
- Phishing Simulations: Run regular simulation to test employee alertness and response capabilities.
- Security Policies: Establish and strictly enforce security policies that mandate the use of secure communication channels and discourage clicking on unverified links.
- Incident Response Planning
Develop and maintain a comprehensive incident response plan to ensure a swift and effective reaction to security breaches:- Incident Response Team: Establish a dedicated team responsible for coordinating the response to security incidents.
- Response Plans: Develop specific plans for different types of breaches, including data exfiltration and ransomware attacks.
- Multi-Factor Authentication (MFA)
Implement Multi-Factor Authentication (MFA) across all email accounts, applications, and devices to provide an essential extra layer of security for user accounts.
Reference
- APT Meets GPT: Targeted Operations with Untamed LLMs
- UTA0388: AI-PoweredTargeted OperationsLeveragingGOVERSHELL
- APT Groups Abuse ChatGPT to Build Advanced Malware and Phishing Kits
- From HealthKick to GOVERSHELL: The Evolution ofUTA0388's Espionage Malware
- APT Hackers Exploit ChatGPT to Create SophisticatedMalware and Phishing Emails
入侵指標 (Indicator of Compromise, IoCs)
URL
IP/Domain
Files
關於 CyCraft
奧義智慧 (CyCraft) 是亞洲領先的 AI 資安科技公司,專注於 AI 自動化威脅曝險管理。其 XCockpit AI 平台整合 XASM (Extended Attack Surface Management) 三大防禦構面:外部曝險預警管理、信任提權最佳化監控,與端點自動化聯防,提供超前、事前、即時的縱深防禦。憑藉其在政府、金融、半導體高科技產業的深厚實績與 Gartner 等機構的高度認可,奧義智慧持續打造亞洲最先進的 AI 資安戰情中心,捍衛企業數位韌性。

