XCockpit
EASM
Anticipate external attack surfaces,
and gain awareness of possible attacks!

Ensure the compliance with cybersecurity standards and regulatory requirements.
Continuously monitor and manage enterprises’ security postures.
Assess and enhance the security management of suppliers.
Assist clients in safeguarding digital security and fulfilling social responsibility.
Evaluate enterprises’ cybersecurity performance within the industry and help align with industry standards.
External Attack Surface Management
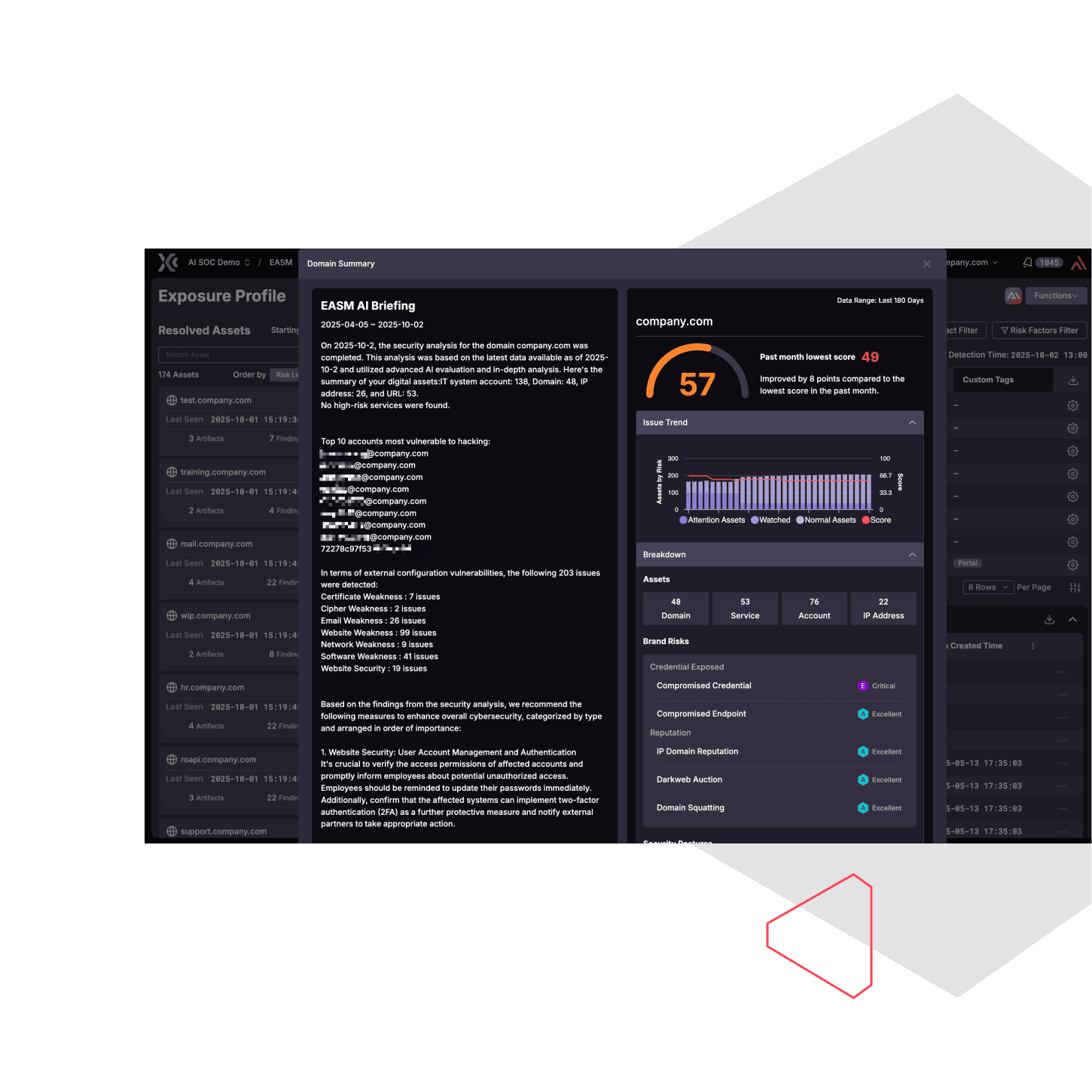
Automatically discover potential external attack surfaces and provide a comprehensive view of digital assets from the hacker's perspective. Proactively identify potential vulnerabilities through in-depth identification and analysis of the entire structure and respective components, correlating the attack surface of accounts, endpoints, and services.
AI-generated Compliance Assessment
An exclusively trained AI model offers practical audit recommendations and risk control measures, tailored to various cybersecurity management systems and regulatory requirements.

Early Warnings
and Leakage Tracing
Leverage AI to inventory legitimate corporate credentials on the surface web, dark web, or public marketplaces, offering real-time alerts and mitigating attacks beforehand.
Continuous Exposure Management
Provide enterprises with intelligence of external assets, manage critical risks through case management, and continuously keep track of diachronic improvement performance.
Autonomous Case Management
Automatically generate tickets of high-severity incidents, track and manage mitigation measures, and record the status and performance of various risk-controlling processes.


Visualized Incident Analysis
Visualize the correlation of external exposure and display according to the risk level and categories of digital assets.
AI Real-time Interpretation
Generate reports of digital asset inventories, supply chain vulnerabilities and subsequent mitigation recommendations based on the overall digital asset overview and external exposure incidents, to help accelerate responding efficiency.

CyCraftGPT
CyCraft's next-gen Cyber AI cybersecurity language model, equipped with professional cybersecurity knowledge as well as case analysis and interpretation capabilities, can assist you in various cybersecurity tasks and improve your team's operational efficiency.

EASM White Paper
In the EASM White Paper, CyCraft inventories 233 cybersecurity issues and categorizes them into 8 major risks. This White Paper provides an in-depth analysis of the reconnaissance activities carried out by most attackers before launching attacks. Enterprises lacking external attack surface management often become primary targets of these attackers.

