【CyCraft Monthly Intelligence】Analysis of Official Security Software CPE Update Package Manipulation

Threat and Impact
The official CPE update package of a well-known Taiwanesecybersecurity software was manipulated. After investigation, the CyCraftresearch team discovered that the attacker used a legitimate packaging tool toembed malicious files into the update process, causing users to experienceunexpected attacks when executing the official update package.
Analyst Perspective
In this incident, attackers used the common Nullsoftpackaging tool. Even though the modified, malicious TexturePackerLib.dll was mixed into the regular update process, the original update completed as expected, makingit difficult for users to detect hidden anomalous activities (such as C2connections, malicious resources downloading, etc.). Therefore, we recommendverifying the signature, hash, and other metadata to ensure the reliance ofexecuted files.
Incident Description
In July 2025, an official CPE update package from awell-known Taiwanese security software vendor was falsified. Duringinvestigation, the CyCraft research team discovered a 20250702_CPE_update.exe executable packaged with the Nullsoft tool. Upon execution, it generated an original CPE_Update.exe and a malicious TexturePackerLib.dll. This behaviorappears to be a normal update program with a valid digital signature butactually conceals the following malicious operations:
- Background Execution: When CPE_Update.exe is executed, it launches the validly signed TexturePacker.exe in the backgroundwhile creating a folder containing the malicious TexturePackerLib.dll.
- Command and Control (C2): Attackers use Google Sheets API (URL: https://sheets.googleapis.com/v4/spreadsheets/1eAYKk9buUngvIXPF5QABMw0fjJ0NCh0g2KmZmhEeGZo) as a C2 server and leverage Google Drive API for datatransmission.
- DNS Monitoring: Later,attackers send DNS queries to gapi.n2p.eyes.sh which issuspected to be used for logging IP addresses of infected hosts.
- Malicious Components: These components contain an unsigned malicious module TexturePackerLib.dll written in Golanguage, used for decrypting configuration files and data exfiltration.
Technical Details
Initial Access
- T1204.002 – User Execution: MaliciousFile
- Exploit legitimate softwareNullsoft to conceal malicious behavior, inducing users to execute what appearsto be a normal update program.
Execution
- T1204 – User Execution
- Users execute the tamperedexecutable 20250702_CPE_update.exe for updates, simultaneously running the legitimate CPE_Update.exe and TexturePacker.exe which only executesin the background.
- T1574.002 – Hijack Execution Flow: DLLSide-Loading
- Execute TexturePacker.exe in the background,loading the malicious module TexturePackerLib.dll through DLL side-loading.

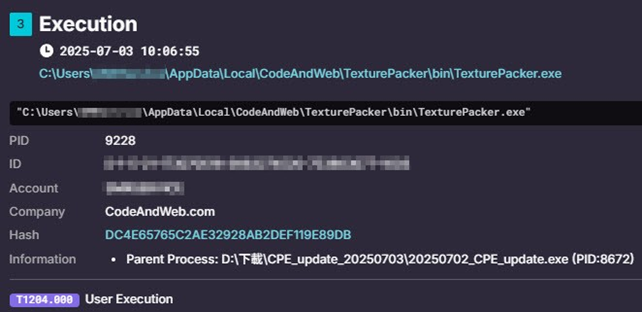
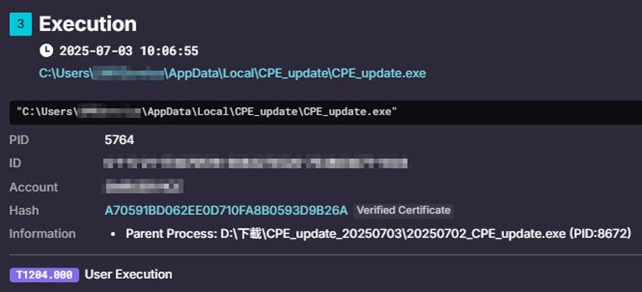
Persistence
- T1543.003 - Create or Modify SystemProcess: Windows Service
- Create a background servicethrough TexturePackerLib.dll to ensure the malicious program continues executing after systemrestart.
Defense Evasion
- T1553.002 - Subvert Trust Controls: Code Signing
- Use digital signatures to hidemalicious components, disguising as legitimate software to evade detection.
- T1071.001 - Application Layer Protocol:Web Protocols
- Conceal C2 traffic throughGoogle Sheets/Drive APIs, making communication behavior appear normal.
Discovery
- T1046 - Network Service Scanning
- Monitor IP addresses ofinfected hosts through DNS queries to gapi.n2p.eyes.sh for subsequent lateral movement.
Collection
- T1082 - System Information Discovery
- Collect system informationincluding hostname, IP, OS version, and privileges after decrypting embeddedconfiguration files.
Command and Control (C2)
- T1071.001 - Application Layer Protocol:Web Protocols
- Use Google Sheets as C2 server,receiving commands through APIs.
Exfiltration
- T1567.002 - Exfiltration to CloudStorage
- Exfiltrate data through GoogleDrive API, using legitimate services to hide data theft activities.
Mitigation
- Block C2 Communications: Block gapi.n2p.eyes.sh and unnecessarycommunications to Google Sheets/Drive APIs at the firewall or DNS level.
- Update and Verification: Ensure all software updateprograms (such as CPE_Update.exe) are from official sources and verify digital signatures.
- Monitor Anomaly: Detect background execution of TexturePacker.exe or unsigned TexturePackerLib.dll. Monitor anomalous requests toGoogle Sheets/Drive APIs.
- Deploy EDR Tools: Use endpoint defense tools supporting YARA rules to detect Go language malware.
IoCs (Indicator of Compromise)
- Domain
gapi.n2p.eyes.sh
- URL
https://sheets.googleapis.com/v4/spreadsheets/1eAYKk9buUngvIXPF5QABMw0fjJ0NCh0g2KmZmhEeGZo - File Hash
- YARA Rules
- Go_TokenDecrypt_JSONUnmarshal (Matching the Go language’s decryption and JSONparsing behavior)
rule Go_TokenDecrypt_JSONUnmarshal
{
meta:
author = "oalieno"
description = "Go malware that decrypts config and uses JSONUnmarshal"
version = "2.0"
strings:
$decrypt_sequence = {
8D 05 ?? ?? ?? ??
89 44 24 44
8B 44 24 3C
89 44 24 48
8D 44 24 44
89 44 24 4C
C6 44 24 27 01
8B 44 24 38
8B 08
83 F9 02
0F 83 ?? ?? ?? ??
}
$json_unmarshal = {
8D 0D ?? ?? ?? ??
89 4C 24 0C
89 44 24 10
E8 ?? ?? ?? ??
}
condition:
all of them
}
About CyCraft
CyCraft is a cybersecurity company founded in 2017, focusing on autonomous AI technology. Headquartered in Taiwan, it has subsidiaries in Japan and Singapore. CyCraft provides professional cybersecurity services to government agencies, police and defense forces, banks, and high-tech manufacturers throughout the Asia-Pacific region. It has received strong backing from the CID Group and Pavilion Capital, a Temasek Holdings Private Limited subsidiary.

