【CyCraft Monthly Intelligence】RedNovember Expansion: Leveraging Pantegana and Cobalt Strike to Infiltrate Global Government and Defense Supply Chains

Threat and Impact
RedNovember, previously known as TAG-100 and highly overlapped with Storm-2077, has been confirmed as a state-sponsored cyber-espionage group operating under Chinese government’s support. The group targets high-profile governments, IGOs, and private entities globally, employing the Go-based backdoor Pantegana alongside open-source tools such as Cobalt Strike and SparkRAT for reconnaissance, initial access, and subsequent intrusions.
Between June 2024 and July 2025, RedNovember extended its targets to organizations in the defense, aerospace, space agency, and legal sectors. The group has demonstrated a capability to compromise edge devices to gain initial access, aiming perimeter security platforms including SonicWall, Cisco ASA, F5 BIG-IP, and Palo Alto Networks GlobalProtect.
Analyst Perspective
RedNovember victims are mainly the aerospace, defense, and government sectors. One of the Taiwanese victim locates at a military air base that also serves as a semiconductor RD facility, suggesting the attacker's intent is of national strategic significance. Furthermore, the timing of attacks coincide with large-scale Chinese military exercises against Taiwan, indicating a simultaneous stress test of Taiwan's digital defenses while simulating cyber warfare capabilities.
Incident Description
RedNovember utilizes a dual strategy to lower their entry barrier by weaponizing PoC exploits and incorporating open-source post-exploitation frameworks like Pantegana. This approach enables less technically sophisticated actors to launch attacks while allowing advanced groups to rapidly scale up operations. The organization has employed these tools for reconnaissance against multiple sensitive targets worldwide and may have achieved successful intrusions across government agencies, defense contractors, IGOs, law firms, and media organizations.
Technical Details
Reconnaissance
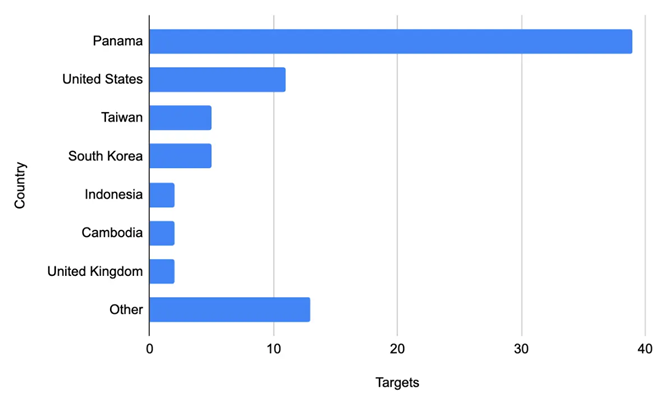
RedNovember extensively targets edge devices to gain initial access. Targets include SonicWall, Cisco ASA, F5 BIG-IP, Palo Alto Networks GlobalProtect, Sophos SSL VPN, and Fortinet FortiGate. The group has focused its reconnaissance on organizations in the government, defense, aerospace, and technology sectors across the United States, Taiwan, South Korea, and Panama.
Resource Development
RedNovember leverages the open-source backdoors Pantegana and Cobalt Strike, delivered malicious payload via SparkRAT. They use LESLIELOADER to load these tools into memory to evade any defense. Additionally, they utilize commercial VPN services like ExpressVPN and Warp VPN to manage their Command and Control (C2) infrastructure.
Initial Access
RedNovember's primary method for gaining initial access is by exploiting vulnerabilities in boundary-layer devices such as firewalls, VPNs, and email servers. They focus on newly disclosed edge device vulnerabilities to establish a foothold within the target organization for deeper exploitation and data theft.
Execution
The group uses Cobalt Strike and SparkRAT to execute malicious code, enabling in-memory execution on both Windows and Linux hosts. RedNovember deploys PoC attacks and weaponized tools to issue commands and maintain persistence over compromised systems.
Command and Control (C2)
RedNovember uses Pantegana to establish encrypted HTTPS C2 channels for transferring files, collecting system fingerprint data, and executing commands. Furthermore, they rely on Cobalt Strike for C2 communication and post-exploitation activities, reinforcing control over the compromised systems.
Overall, RedNovember conducts cyber-espionage attacks against high-value organizations globally by combining open-source tools, weaponized PoC programs, and customized loaders. The group strategically targets edge devices as the initial intrusion vector and maintains long-term persistence through covert Command and Control (C2) communication, demonstrating a highly mature attack capability that poses a persistent and significant threat to the global security landscape.
Mitigation
In response to RedNovember's diverse tactics, enterprises must adopt multi-faceted measures encompassing detection, prevention, and response strategies.
Collect Related Indicators of Compromise (IoCs)
Integrate relevant IoCs associated with RedNovember's activities to preemptively defend their attacks.
Detect and Block Malicious Infrastructure
Proactively monitor and block malicious infrastructure linked to RedNovember, such as the C2 servers for Pantegana, SparkRAT, and Cobalt Strike.
Patch Vulnerabilities
Prioritize patching high-risk and actively exploited vulnerabilities, especially those affecting externally facing perimeter devices, to prevent exploitation by groups like RedNovember.
Configure Network Defense Mechanisms
Deploy Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and other network defenses. Refer to the IoC chaper for external IPs and domains to generate alerts and block connections to known RedNovember C2 infrastructure.
Regularly Audit External-Facing Devices
Conduct routine audits of all external connection and boundary devices to reduce exposed attack surfaces. Disable unnecessary interfaces or portals and restrict devices to essential services required for business operations.
Conclusion
By adhering to these mitigation strategies, enterprises can strengthen their resilience against threat actors like RedNovember and reduce the risk of cyber-espionage targeting the government, defense, and technology sectors. Stay alerted, monitor proactively, and deploy timely incident response are critical elements for establishing an effective cybersecurity defense.
Reference
- RedNovember Targets Government, Defense, and Technology Organizations
- RedNovember Hackers Breach Government and Technology Networks to Install Backdoors
- Chinese Cyberespionage Group RedNovember Targets Global Defense and Government Organizations
- Hunt for RedNovember: Beijing hacked critical orgs in year-long snooping campaign
- RedNovember Hackers Targeting Government and Tech Organizations to Install Backdoor
IoCs (Indicator ofCompromise)
Domain
aeifile[.]offiec[.]us[.]kg
citrix[.]offiec[.]us[.]kg
cna[.]offiec[.]us[.]kg
download[.]offiec[.]us[.]kg
gp[.]offiec[.]us[.]kg
login[.]offiec[.]us[.]kg
test[.]offiec[.]us[.]kg
vpn[.]offiec[.]us[.]kg
vpn1[.]offiec[.]us[.]kg
RedNovemberPantegana C2 IP Addresses
45[.]61[.]187[.]124
198[.]98[.]50[.]218
198[.]98[.]53[.]163
198[.]98[.]61[.]155
209[.]141[.]37[.]254
205[.]185[.]126[.]208
205[.]185[.]124[.]24
209[.]141[.]42[.]131
209[.]141[.]46[.]83
209[.]141[.]57[.]116
RedNovemberCobalt Strike C2 IP Address
47[.]103[.]218[.]35
RedNovemberCobalt Strike C2 URLs
hxxp://47[.]103[.]218[.]35/pixel
hxxp://47[.]103[.]218[.]35/GSjY
File Hash
About CyCraft
CyCraft is a cybersecurity company founded in 2017, focusing on autonomous AI technology. Headquartered in Taiwan, it has subsidiaries in Japan and Singapore. CyCraft provides professional cybersecurity services to government agencies, police and defense forces, banks, and high-tech manufacturers throughout the Asia-Pacific region. It has received strong backing from the CID Group and Pavilion Capital, a Temasek Holdings Private Limited subsidiary.

