STARTS FROM
CyCraft is an AI company that forges the future of cybersecurity resilience through autonomous systems and human-AI collaboration.
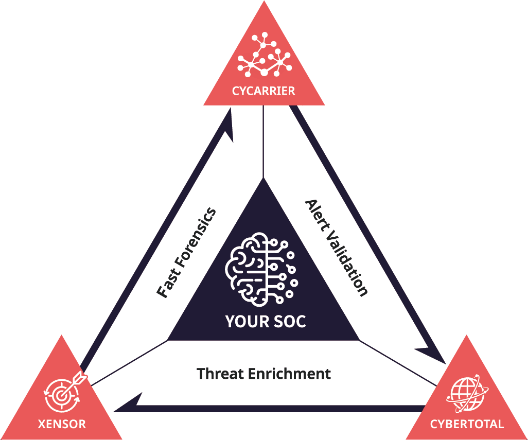
CyCraft AIR has taken the next step and integrated ground-breaking AI into every level of monitoring, detection, investigation, and response, giving your SOC the proven advantage against the world’s most sophisticated adversaries.

CyCraft AIR has taken the next step and integrated ground-breaking AI into every level of monitoring, detection, investigation, and response, giving your SOC the proven advantage against the world’s most sophisticated adversaries.
COMPROMISE ASSESSMENT
Our CA Service team walks you step-by-step through your CA report, which includes a complete site-wide analysis of risks and exposures, security hygiene issues, and suspicious behavior analysis.
INCIDENT RESPONSE
In less than 1 day, not only receive your fully actionable digital forensic incident response (DFIR) report but get it explained to you in granular detail directly from our DFIR Service team.
MANAGED DETECTION AND RESPONSE
CyCraft MDR is uniquely designed to provide fully actionable reports on detected malicious behavior while continuously monitoring and managing the cyber situation of even large-scale enterprises with thousands of endpoints.
SECURE FROM HOME
CyCraft SFH services go beyond legacy preventive solutions by providing you granular visibility into your current org-wide cybersecurity situation in real-time while detecting hidden devices, lateral movement, and malicious behavior.

When you join the CyCraft Community, you’re in good company. CyCraft provides organizations worldwide with the innovative AI-driven technology necessary to stop cyber threats in the 2020s.
The CyCraft AIR platform is uniquely designed to detect the latest trends in malicious behavior, automate investigations, and auto-triage alerts, allowing CyCraft customers to detect, track, contain, and eradicate threats in real-time.
CYCRAFT ACCELERATED
PARTNERS
Raise
Resilience
With CyCraft Japan
Fast / Accurate / Simple / Thorough
Stay
Cyber Fit
With CyCraft Japan
Fast / Accurate / Simple / Thorough
Raise
Resilience
With CyCraft Japan
Fast / Accurate / Simple / Thorough
Stay
Cyber Fit
With CyCraft Japan
Fast / Accurate / Simple / Thorough
WHY CYCRAFT?
INDUSTRY RECOGNITION
In the past year, CyCraft outperformed all other MITRE ATT&CK® Evaluation vendors in Technique, Tactic, and General detections with zero configuration changes. CyCraft AIR and CyberTotal both received the Best of Show Grand Prize Award for Security Solutions at Interop Tokyo 2020; CyCraft also received 20+ 2020 Cybersecurity Excellence awards in categories including Managed Detection and Response, Incident Response, Threat Intelligence, and Artificial Intelligence. CyCraft is a proud member of FIRST, a premier organization for incident response security teams.





COMPETITIVE SOLUTIONS
MITRE ATT&CK Evaluations Validates Industry Leadership for CyCraft AIR Managed Detection and Response. CyCraft AIR scored more real-world GTT detections (General, Tactic, and Technique) than any other vendor solution and with zero configurations.
ANALYST RECOGNIZED
for intelligence-led Cybersecurity by leading global research firm IDC.

ISO/IEC 27001 CERTIFICATION
CyCraft is certified for ISO/IEC 27001:2013 certification, demonstrating CyCraft’s consistent commitment to thoroughly evaluating security risks, the design and implementation of controls, and the maintenance of effective processes to manage security. Everything Starts From Security
Why Pick US?
“CyCraft’s customer support provided excellent communication, incident reports, and response times, leaving us feeling confident and at ease with our security situation”
“10/10! From deployment to operations this had been the EDR solution that we truly needed. ”

“10/10! From deployment to operations this had been the EDR solution that we truly needed. ”

PROUD TO PROTECT
TAIWAN CRITICAL
INFRASTRUCTURE
The CyCraft Community is our Priority.
Everything Starts From Security.







PROUD TO PROTECT
TAIWAN CRITICAL
INFRASTRUCTURE
The CyCraft Community is our Priority.
Everything Starts From Security.

CYCRAFT
IS TRUSTED BY
Fortune 500
Companies
Financial
Institutions
Law
Enforcement
Government
Agencies
Critical
Infrastructure
Airlines
Manufacturing
Hi-Tech
Telecoms
S0Cs
Many more…
CYCRAFT
IS TRUSTED BY

Your CyCraft representative is standing by to help you with an incident or answer any question regarding our incident response, compromise assessment, or managed detection and response products and services.
